So I took some time on my sunday to hack my TL-WR710N(US) edition, and I had a lot of fun. The first thing I got to do was take it apart! I was able to find the serial headers too, just a little soldering to make it work!
So opening the unit wasn’t a treat, I don’t really know how I could open it without messing up the case, oh well.
This is what the board looks like popped out of the case.
Flipping it over revealed the TP_IN and TP_OUT ports.

A quick Google search revealed those were serial port connections… I am going to to lie I got a bit giddy!
I then slowly but surely put it all back together, I clipped a bit of the plastic power light off to fit the wires out of the case.

I then had to hot glue the light in place (I have mad hot glue gun skills):

Then put the case on top but first I had to slightly modify the piece that goes down the center:

Using my spark fun ftdi I booted the machine using 115200 8n1 first try was a success!

I had no idea what the password was, so I just headed straight to openwrt to get one of those images.
I used the default tp-link upgrader to upgrade, but I watched in the console to see what happened.
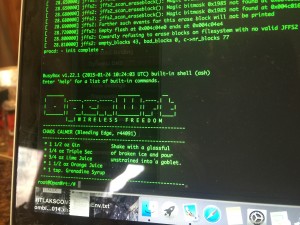
It then magically rebooted into openwrt!
That was all fun and stuff, but I wanted to do something interesting. I toyed around with a few ideas, one was building an iBeacon out of TP-Link:
Cool that was fun, but what would be more fun? How about Tor!
I was familiar with this project: https://github.com/grugq/portal but my WR710N(US) edition wasn’t supported… Damn.. So I tried installing tor,
opkg install tor |
and I couldn’t figure out why the system kept crashing and rebooting (thus removing everything), Since I got a few seconds of leeway before the crash I got real fast, and typed top, I saw tor keep filling up all avalible ram. AH HA! I had it, so what was I to do? Well the TP-Link has a USB connector on the bottom for 3G/4G etc, I decided to make some swap space for the device on the memory stick. Now in short I present you running openwrt on the TP-Link TL-WR710N(US)
This is assuming that you have connected to the internet port on the LAN/WAN connection
opkg update opkg install swap-utils opkg install zram-swap opkg install kmod-usb-storage opkg install kmod-usb-storage-extras opkg install usbutils modprobe sd_mod modprobe usb-storage |
At this point you can connect your USB device, and it should pop up and say the device name. in my case is was sda1
WARNING: THE FOLLOWING COMMANDS WILL WIPE YOU USB DRIVE
mkswap /dev/sda1 swapon /dev/sda1 |
Alright we now have enough to install tor:
opkg install tor |
Now we need to make it so anything that connects to wifi is automatically on Tor.
first we edit the network file and add these lines to the bottom
vi /etc/config/network |
config interface 'tor' option proto 'static' option ipaddr '172.16.1.1' option netmask '255.255.255.0' |
Now we need to edit the radio file, unfortunately on the WL710N it only has one radio some models have 2 and 2.4 and a 5ghz, so we could put tor on one and regular access on another. Oh well anyways!
vi /etc/config/wireless |
The Whole file will contain this:
config wifi-device radio0
option type mac80211
option channel 11
option hwmode 11g
option path 'platform/ar933x_wmac'
option htmode HT20
config wifi-iface
option device radio0
option network tor
option mode ap
option ssid 'The Dark Web!'
option encryption none |
Now we need to make our firewall rules.
vi /etc/config/firewall |
The whole file will look like this:
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option masq '1'
option mtu_fix '1'
option network 'wan'
config zone
option name 'tor'
option network 'tor'
option input 'REJECT'
option output 'ACCEPT'
option forward 'REJECT'
option conntrack '1'
config rule
option name 'Allow-Tor-DHCP'
option src 'tor'
option proto 'udp'
option dest_port '67'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Tor-DNS'
option src 'tor'
option proto 'udp'
option dest_port '9053'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Tor-Transparent'
option src 'tor'
option proto 'tcp'
option dest_port '9040'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Tor-SOCKS'
option src 'tor'
option proto 'tcp'
option dest_port '9050'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config forwarding
option dest 'wan'
option src 'lan'
config include
option path '/etc/firewall.user' |
Now we edit the user script for some custom rules.
vi /etc/firewall.user |
The whole file will look like this
iptables -t nat -A PREROUTING -i wlan0 -p udp --dport 53 -j REDIRECT --to-ports 9053 iptables -t nat -A PREROUTING -i wlan0 -p tcp --syn -j REDIRECT --to-ports 9040 |
Now we need to edit the tor config file:
vi /etc/tor/torrc |
This goes at the end of the file:
DNSPort 9053 AutomapHostsOnResolve 1 AutomapHostsSuffixes .exit,.onion DNSListenAddress 172.16.1.1 TransPort 9040 TransListenAddress 172.16.1.1 |
Last thing is restarting some services:
/etc/init.d/network restart ifup wlan0 /etc/init.d/firewall restart /etc/init.d/tor restart |
After that go to your computer/phone whatever and select “The Dark Web!” first site to hit is:
https://check.torproject.org
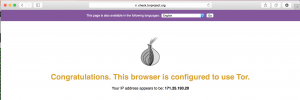
If it worked you should get something like this:
That’s it your on tor, we ONLY redirected DNS and TCP, so most of UDP is not sent over the tor network.
The speed seemed ok to me, probably not something I would use all the time, but it was a fun Sunday experiment!
Have Fun!
John “Hide it” Hass
P.S. an untested way to backup the firmware
cat /dev/mtd5 > /tmp/firmware.bin |
Of course if you’re out of space you can send it over scp:
dd if=/dev/mtd5 | ssh user@x.x.x.x 'dd of=~/firmware.bin' |
Restore by first copying the firmware to /tmp/ and executing
mtd -r write /tmp/firmware.bin linux |
I don’t plan on keeping tor as my main usage for this device.